Integrating Active Directory Users into KACE
- Creation of KACE roles
- LDAP configuration
- User import
- Creating a label for users
- Creating a label for computers
AD Integration
Creation of KACE Roles
- Before importing users, it is necessary to create roles within the SMA.
- In Settings > Role, create roles based on the permissions you wish to grant on the appliance.
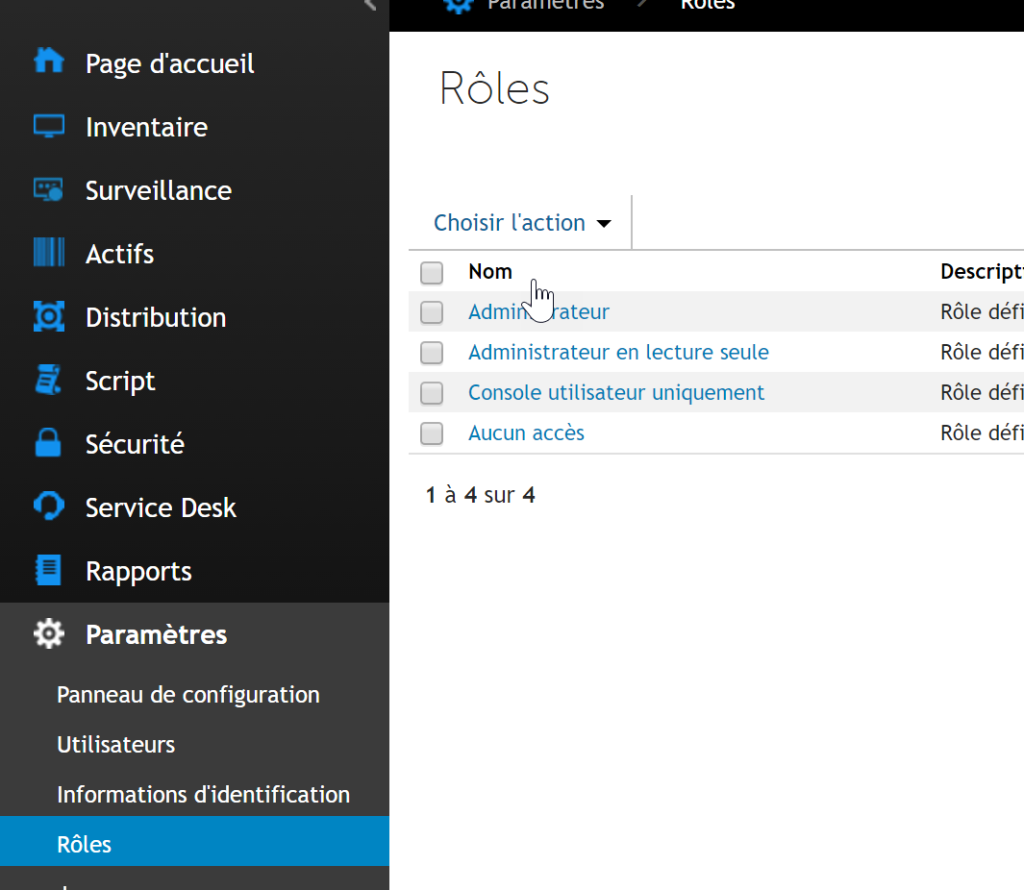
- Since default roles are not modifiable, it is advisable to duplicate an existing role to customize it according to your needs.
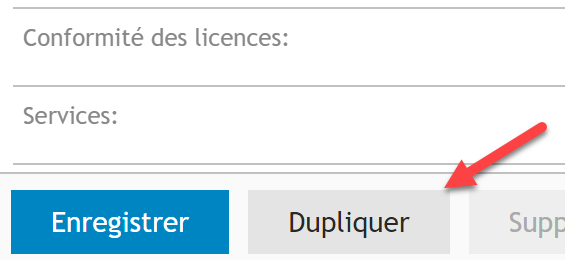
- Here are the rights available by tab:
- Read
- Write
- Hide
LDAP Authentication
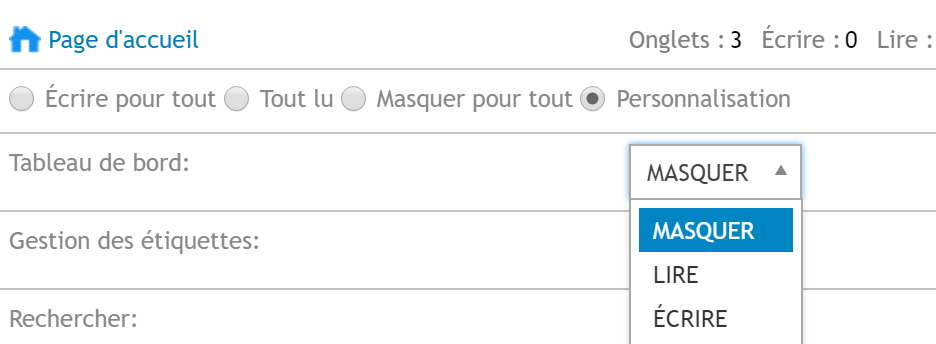
- Go to Settings > Control Panel > User Authentication
Three types of servers are available by default.
- Admin server
- Read-only admin server
- User server
Warning: Never retain unconfigured servers.
- In this example, I will retain only the user configuration. The other two configurations will be deleted (this is mandatory for the functionality to work).
Example configuration (labosd.lan being my domain name)
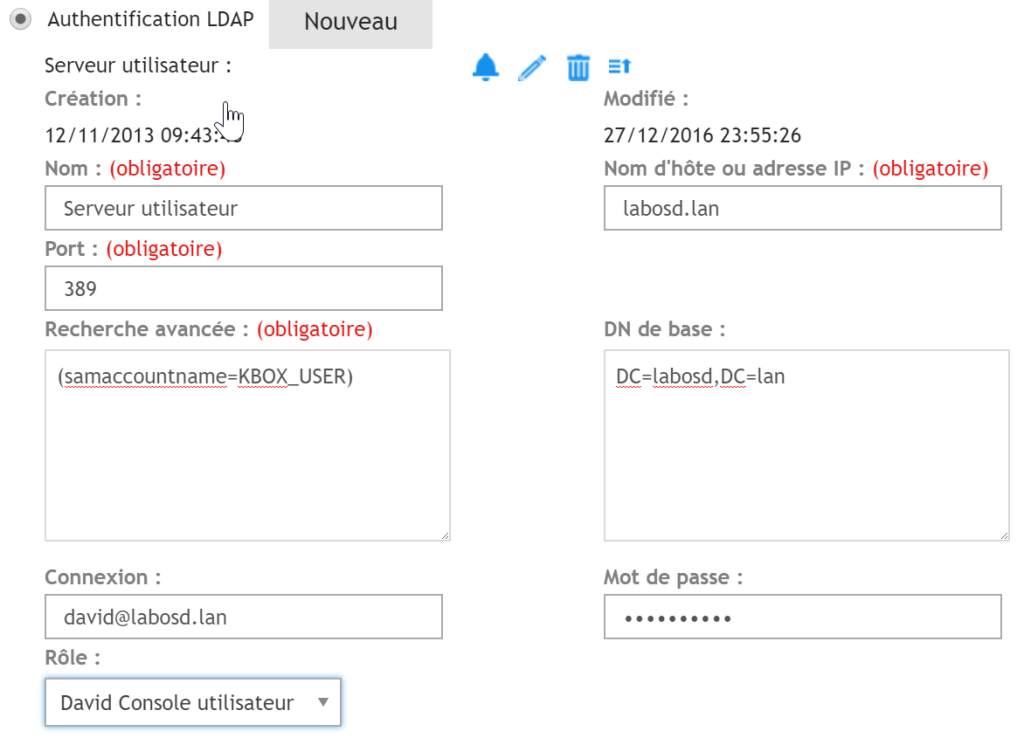
When a user logs onto the Appliance, their user account replaces the variable KBOX_USER.
You can add additional LDAP attributes if needed.
- Users must have a registered email address to be able to log in.
1 | (&(samaccountname=KBOX_USER)(mail=*)) |
- Users must be in the KACE group to log in.
1 | (&(samaccountname=KBOX_USER)(memberOf=CN=KACE,OU=UsersLAB,DC=labosd,DC=lan)) |
- To test the configuration, temporarily replace KBOX_USER with an AD account and then enter the password for that account.
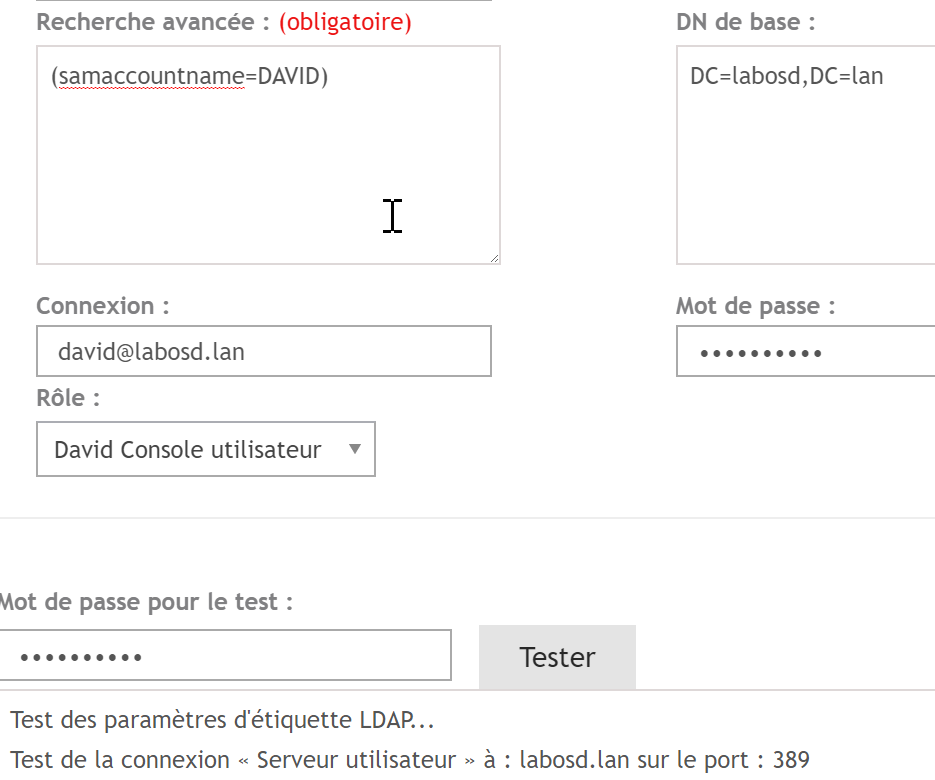
- From now on, users can log onto the Appliance.
User Import
User import is mandatory if you are setting up the Help Desk module.
- Next, schedule the automatic import of users. Click on the small bell/clock icon.
- Select a time for scheduling (note: set this scheduling at a different time than the Appliance backup).
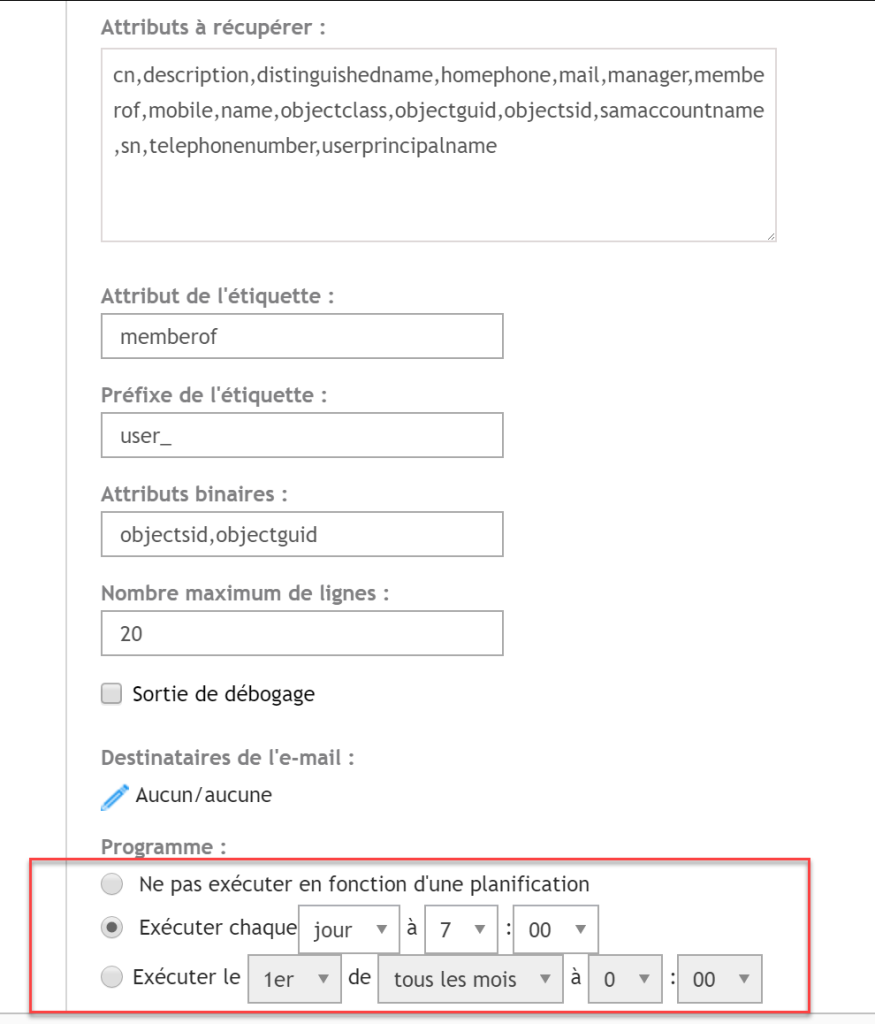
- Click “Next”; on the following screen, make the association between KACE and LDAP. In LDAP UID, you can use the SAMACCOUNTNAME value, which will be the account to be entered on the KACE interface.
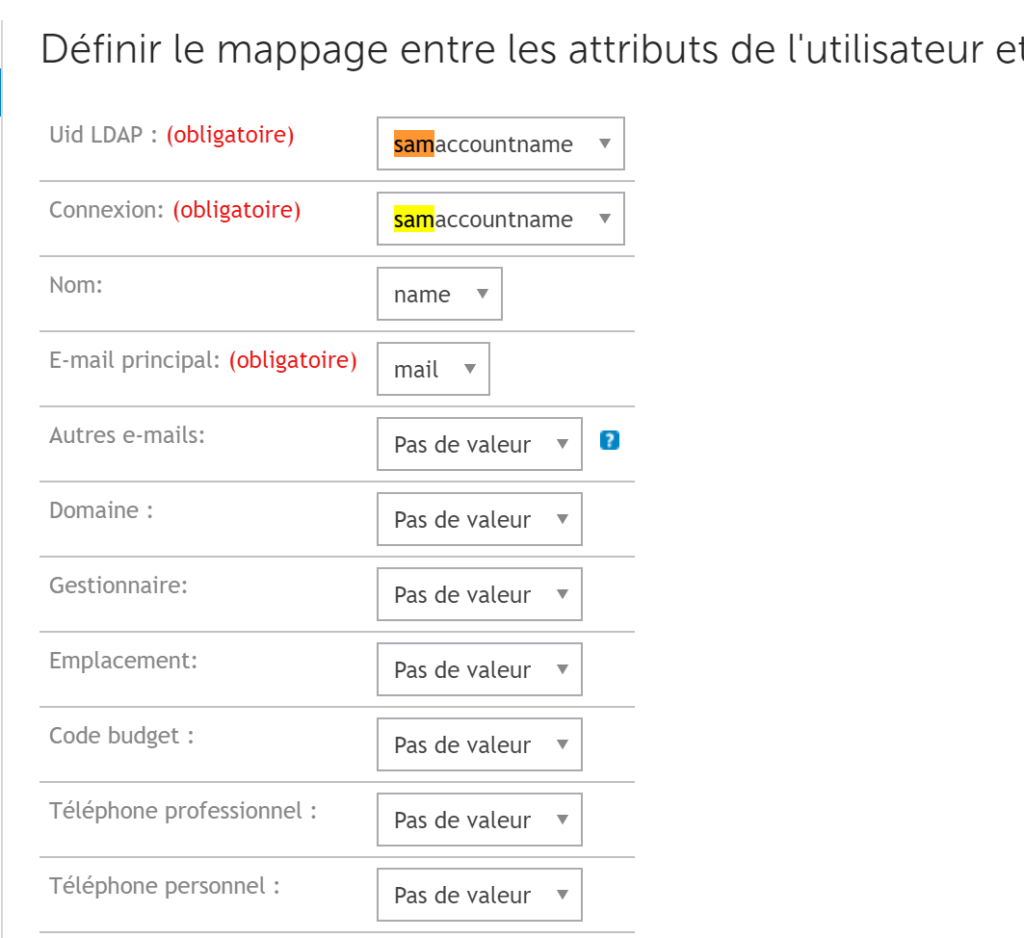
WARNING: If an LDAP attribute that is used does not have a value, the user will not be imported. For example, if you use the email address and this value is not populated, users will not be imported.
Role Assignment on a Case-by-Case Basis
- You can modify the KACE role of one or more users. This change will take precedence over the LDAP configuration.
LDAP Computer Label
- You can also create labels based on LDAP. For example, to install an application on all computers within a specific OU.
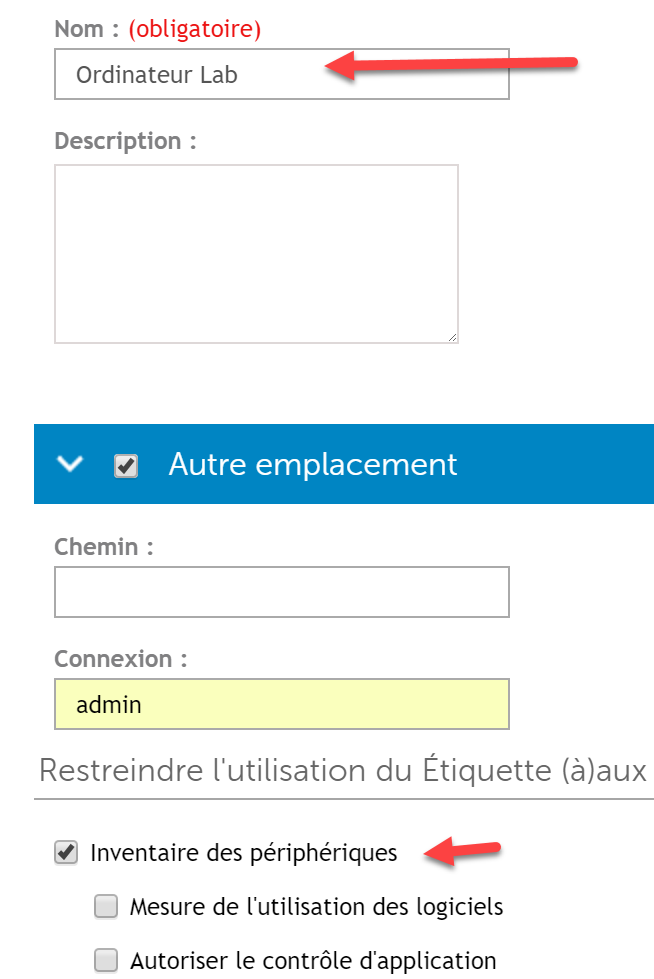
- First, create an empty label. For this, on the home page under Label Management select “Labels.”
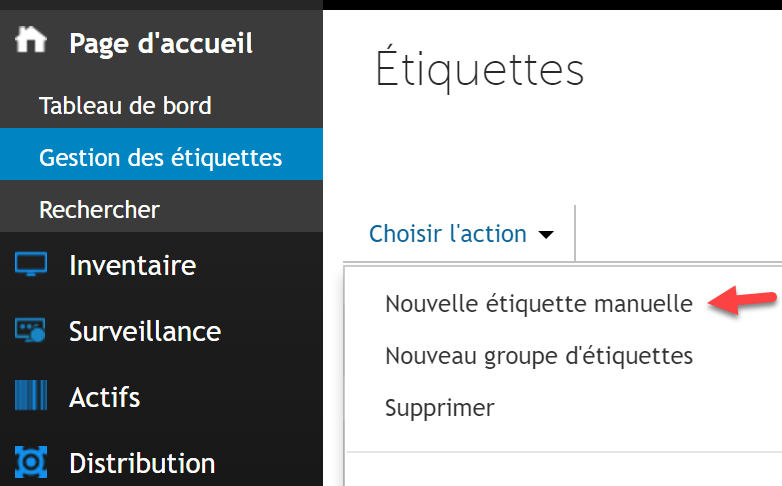
- Select “choose an action” and add a new label.
- In the name, indicate the label name that will be used for the LDAP computer query and check the option “computer inventory” then validate.
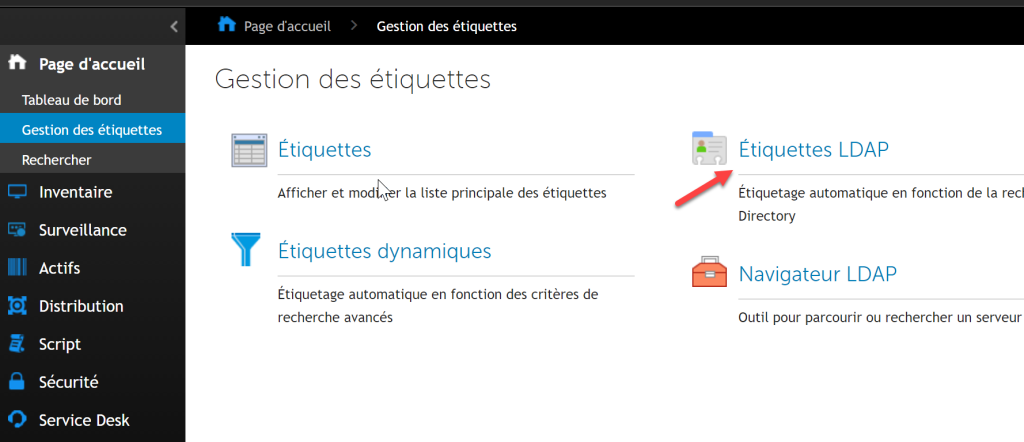
- Then on the home page, select “Label Management” and choose “LDAP Labels“
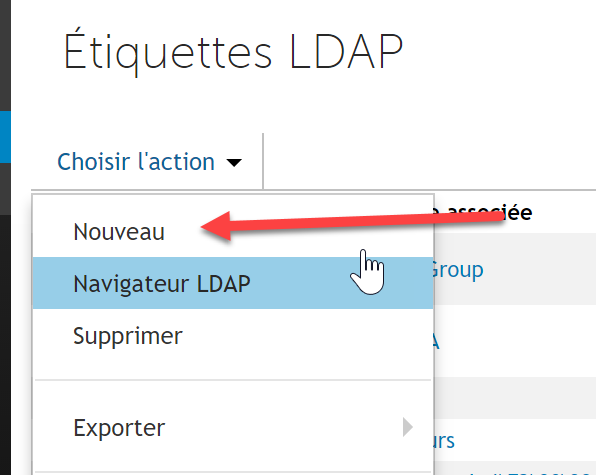
- In “Choose an Action,” select “New”
- Example of an LDAP label for a computer placed in an OU
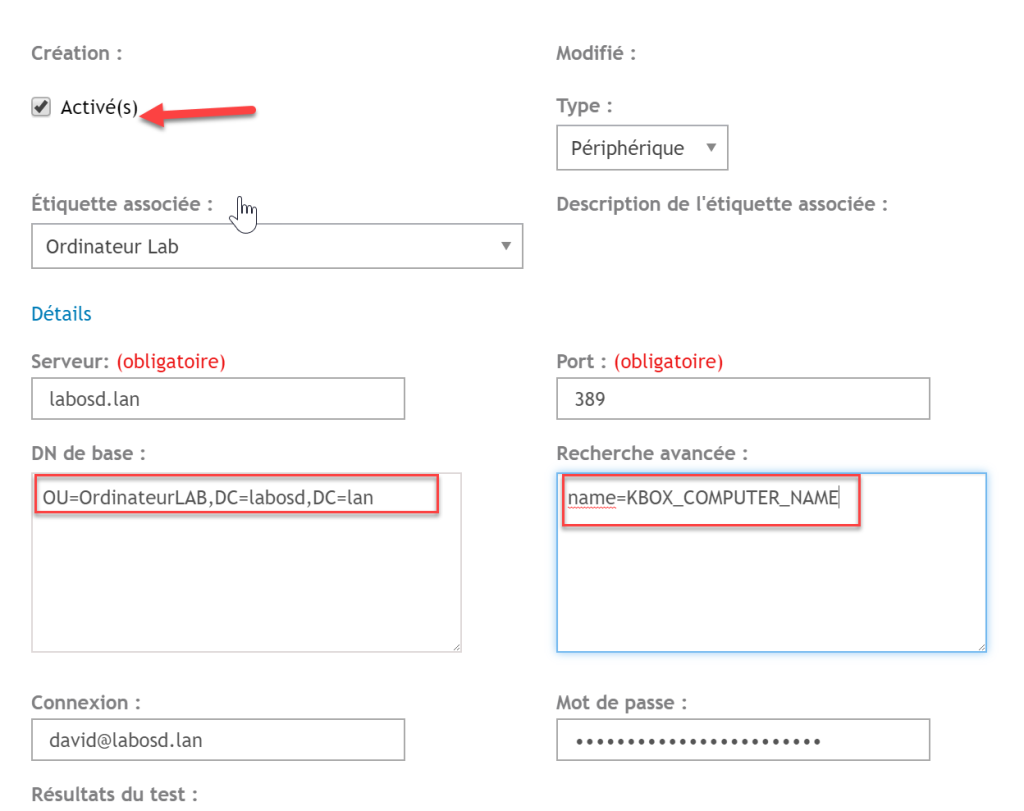
- The computer’s name replaces the variable KBOX_COMPUTER_NAME when the computer connects to KACE
- The computers will be associated with the label during the inventory report
- Do not forget to activate the LDAP label

LDAP User Label
The user will be assigned to the label:
- During the automatic import of users into KACE
- When the user logs into the Appliance
Creating an Empty Label
- Start by creating an empty label. For this, go to the home page and select “Label Management“
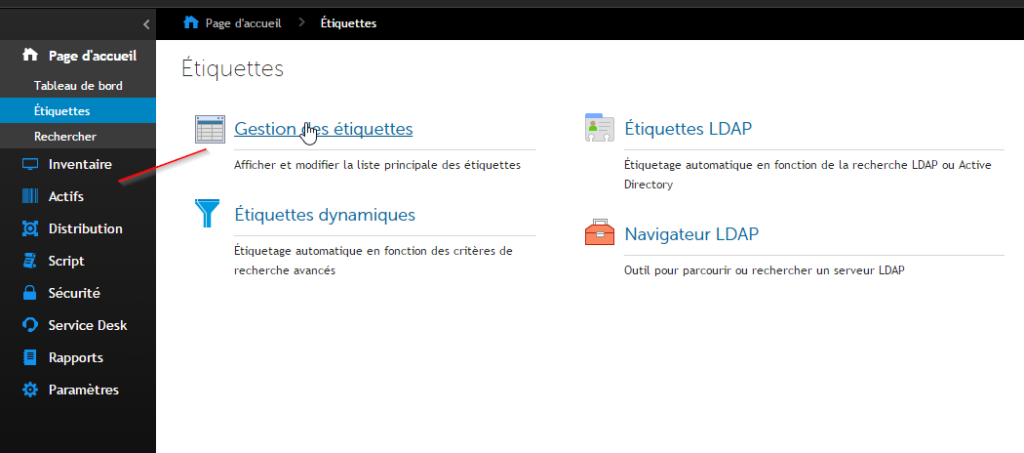
- Select “choose an action” and add a new label.
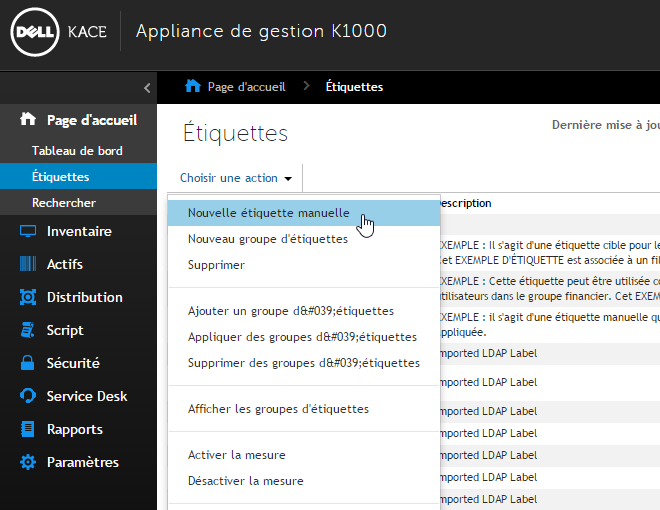
- In the name, specify the label name that will be used for the LDAP computer query and check the option “user inventory” then validate.
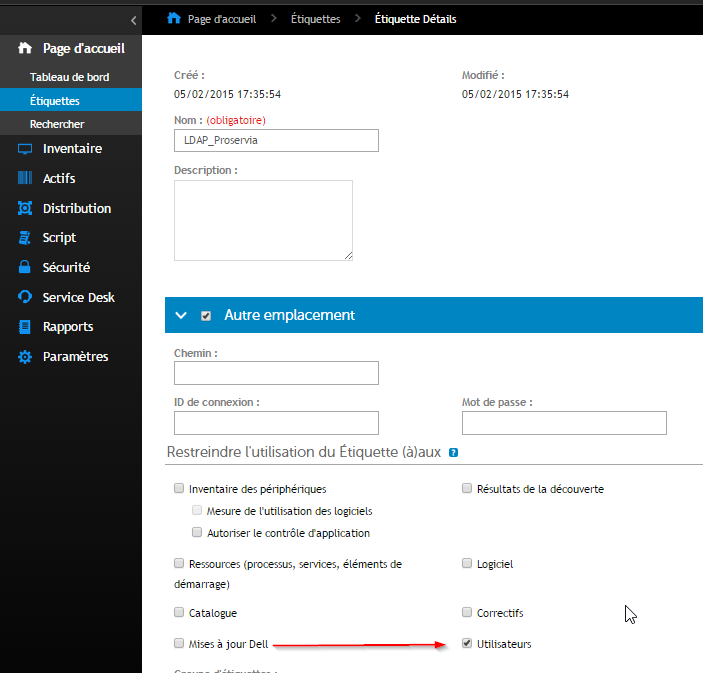
Label Modification
- Go to User Settings (LDAP Authentication)
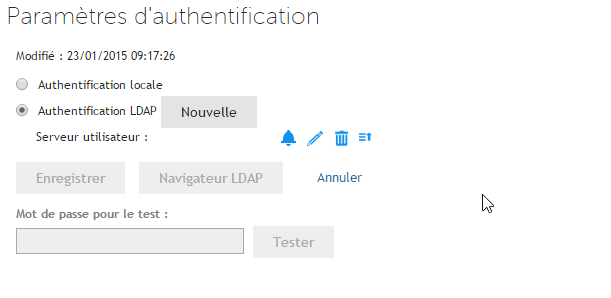
- Click on the bell-shaped icon and check the values:
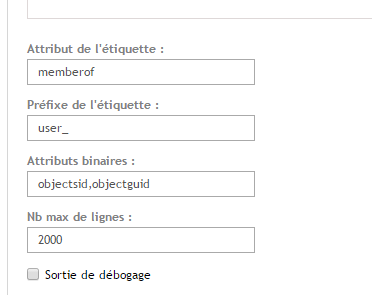
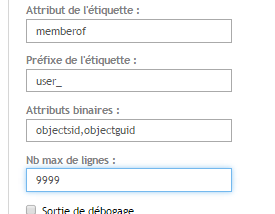
- Label Attribute
- Label Prefix
LDAP Label Based on an OU
- Then on the home page, under Labels, select “LDAP Labels“
- In “Choose an Action“, select “New”
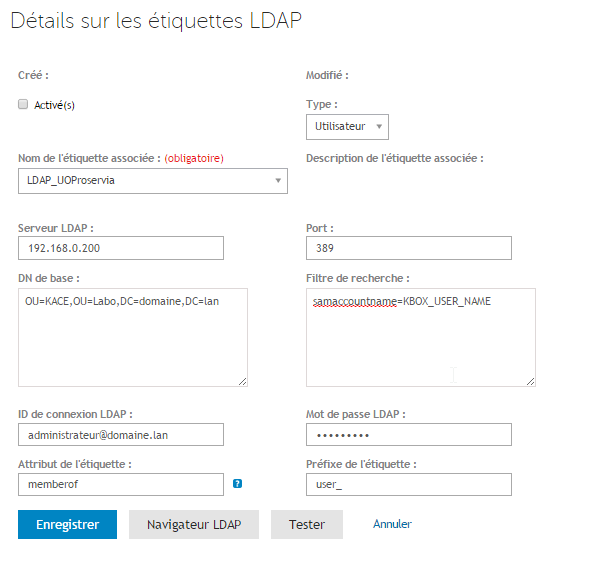
Example of Label
Search Filter: samaccountname=KBOX_USER_NAME
Base DN: OU=KACE,OU=Lab,DC=domain,DC=lan
Record the Label Attribute and the Label Prefix
- Do not forget to activate the LDAP label

LDAP Label Based on a Group
- Then on the home page under Labels select “LDAP Labels“
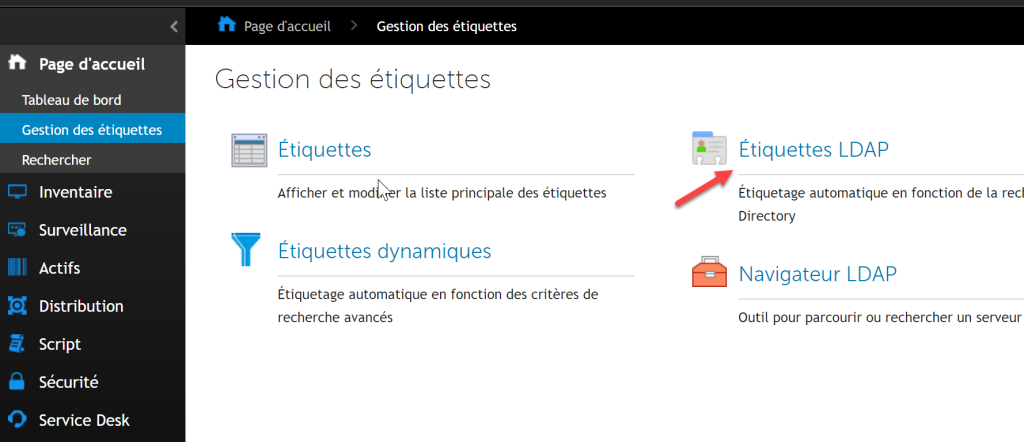
- In “Choose an Action”, select “New”
Example of Label
Search Filter: (&(samaccountname=KBOX_USER_NAME)(memberof=CN=Proservia,OU=KACE,OU=Lab,DC=domain,DC=lan))
Base DN: OU=Lab,DC=domain,DC=lan
Record the Label Attribute and the Label Prefix
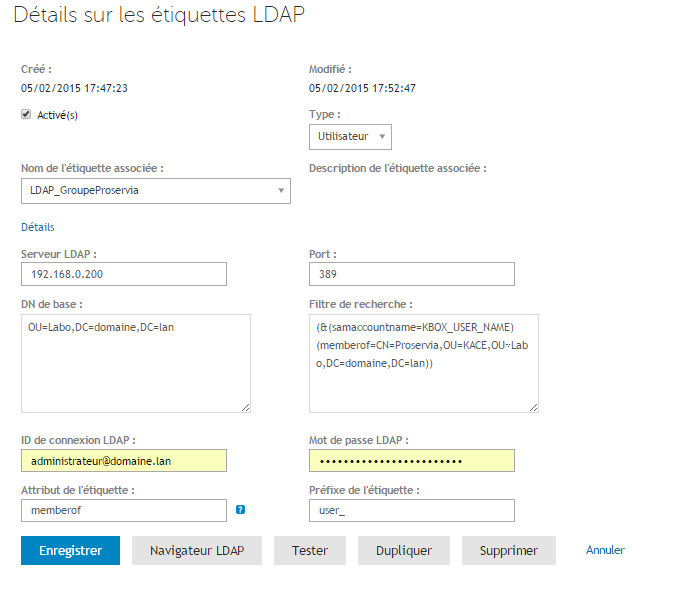
- Do not forget to activate the LDAP label

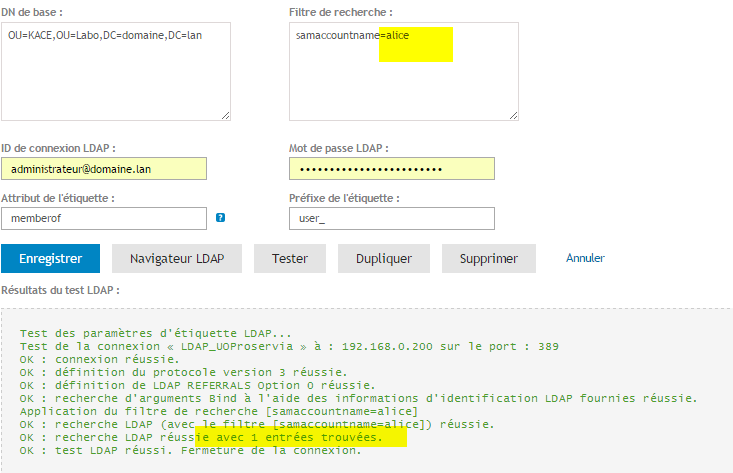
Testing a User Label?
- Replace KBOX_USERNAME with the name (samaccountName) of a person and click on the test button
Appendices
Number of Lines
- If you have a lot of groups in AD, increase the value “Nb max of lines”
List of Variables Usable in LDAP Queries
Machine Filter
- KBOX_COMPUTER_NAME
- KBOX_COMPUTER_DESCRIPTION
- KBOX_COMPUTER_MAC
- KBOX_COMPUTER_IP
- KBOX_USERNAME
- KBOX_USER_DOMAIN
- KBOX_DOMAINUSER
- KBOX_CUSTOM_INVENTORY_*
Example Machine LDAP Filter setup:
Search Base DN: CN=Computers,DC=kace,DC=com
Search Filter setup needs to be evaluated against an LDAP attribute:
(&(name=KBOX_COMPUTER_NAME)(memberOf=CN=BuildingA,DC=kace,DC=com))
or (&(objectCategory=computer)(name=KBOX_COMPUTER_NAME))
Users Filter
- KBOX_USER_NAME
- KBOX_FULL_NAME
- KBOX_EMAIL
- KBOX_DOMAIN
- KBOX_BUDGET_CODE
- KBOX_LOCATION
- KBOX_WORK_PHONE
- KBOX_HOME_PHONE
- KBOX_MOBILE_PHONE
- KBOX_PAGER_PHONE
- KBOX_CUSTOM_1
- KBOX_CUSTOM_2
- KBOX_CUSTOM_3
- KBOX_CUSTOM_4
- KBOX_ROLE_ID
- KBOX_LDAP_UID
Example of User Filter setup:
Search Base DN: DC=kace,DC=com
Search Filter: (&(samaccountname=KBOX_USER_NAME)(objectClass=user))
or (&(samaccountname=KBOX_USER_NAME)(memberOf=CN=Support,OU=Dept,DC=Kace,DC=com))

0 Comments