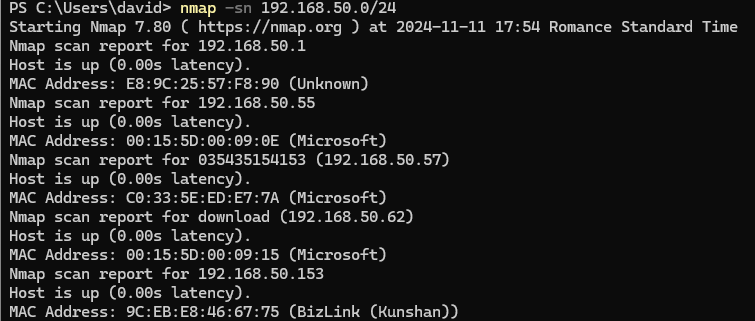
Basic network scan
This command identifies active hosts on a given network.
nmap -sn 192.168.1.0/24
-sn: Disables port scanning to perform a simple ping scan, identifying only active hosts.
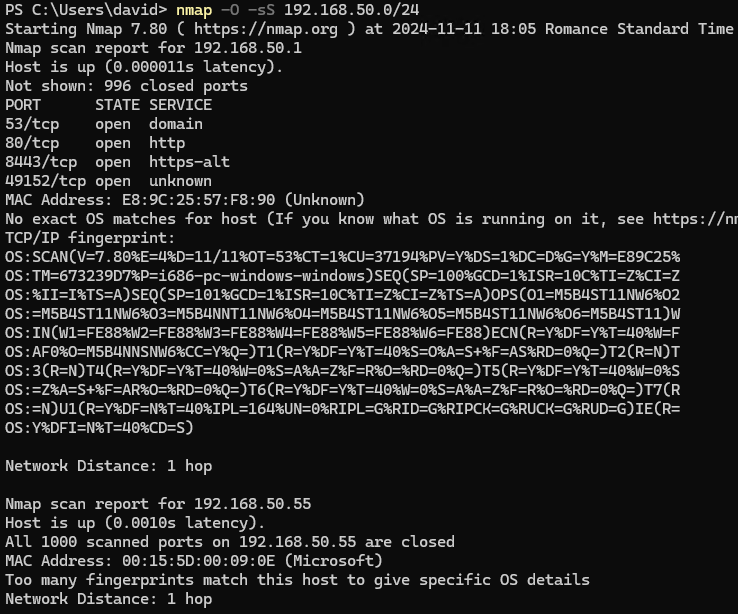
Scan systems and services
This command discovers hosts and gathers information about their operating systems and services.
nmap -O -sS 192.168.1.0/24
-O: Enables OS detection.-sS: Uses SYN scan to detect open ports.
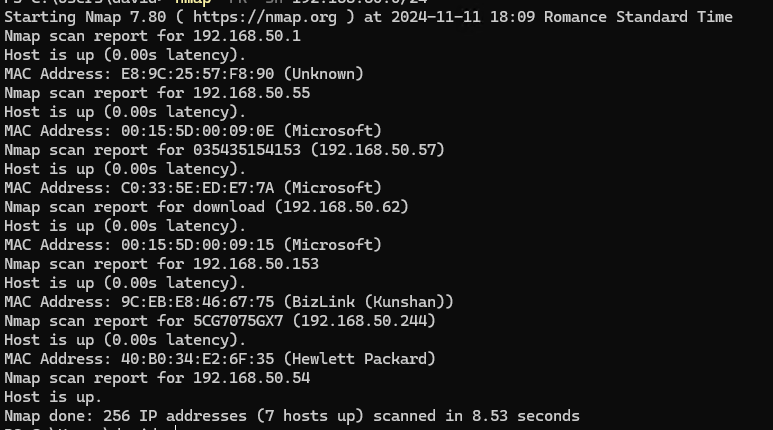
ARP discovery scan
=> recommended for internal VLANs
If you are on the same VLAN, an ARP scan is often more effective for detecting devices.
nmap -PR -sn 192.168.1.0/24
-PR: Uses ARP requests for host discovery, useful for local networks.-sn: Only detects hosts without scanning ports.
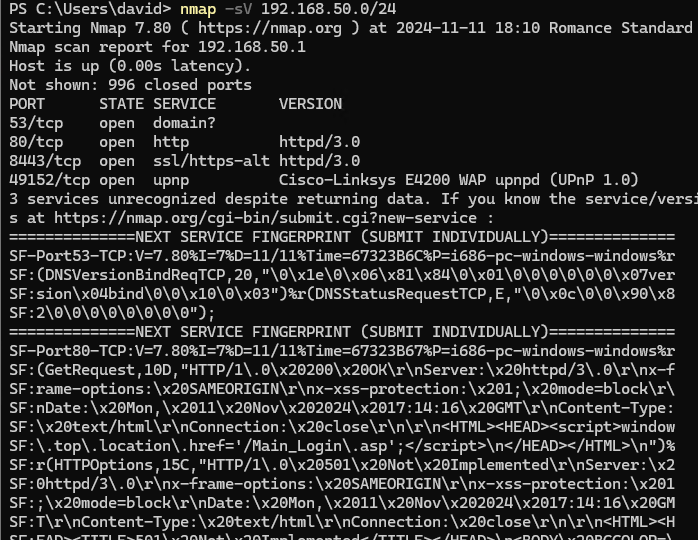
scan with service detection
To identify hosts and scan open ports and services:
nmap -sV 192.168.1.0/24
-sV: Enables service version detection to get detailed information on open ports and running services.
“List scan” mode to list hosts
This command discovers used IP addresses without performing a port scan.
map -sL 192.168.1.0/24
-sL: Simply lists IP addresses in the range without sending packets to the hosts.
Important note
The IP ranges (e.g., 192.168.1.0/24) should be adjusted according to your VLAN configuration.



0 Comments