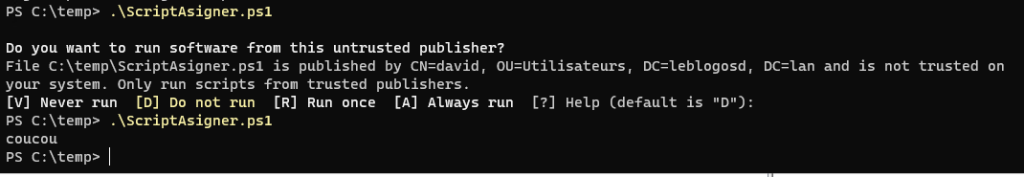
The article provides a guide on how to sign PowerShell scripts using two methods:
- With a Self-Signed Certificate:
- With An Internal PKI
With a self-signed certificate.
Creating the Certificat
- Creating the certificate in PowerShell
$NomSujet = "ScriptPowerShell"
# Create certificate
$MoncertificatPowershell = New-SelfSignedCertificate -FriendlyName "Certificat Powershell auto signe" -Subject $NomSujet -Type CodeSigningCert -CertStoreLocation Cert:\LocalMachine\My -NotAfter (Get-Date).AddYears(10)
# Add certificate to "Autorités de certification racine de confiance"
$rootStore = [System.Security.Cryptography.X509Certificates.X509Store]::new("Root","LocalMachine")
$rootStore.Open("ReadWrite")
$rootStore.Add($MoncertificatPowershell)
$rootStore.Close()
# Add certificate to "Éditeurs approuvés"
$publisherStore = [System.Security.Cryptography.X509Certificates.X509Store]::new("TrustedPublisher","LocalMachine")
$publisherStore.Open("ReadWrite")
$publisherStore.Add($MoncertificatPowershell)
$publisherStore.Close()
Certificate Verification
To verify that the certificate exists
Get-ChildItem Cert:\LocalMachine\My -CodeSigningCert
Script Signature
- To sign the PowerShell script
$Certificat = Get-ChildItem Cert:\LocalMachine\My -CodeSigningCert
$Script = "C:\temp\scriptasigner.ps1"
$TimestampServer = "http://timestamp.comodoca.com/authenticode"
Set-AuthenticodeSignature $Script -Certificate $Certificat -TimestampServer $TimestampServer
- The script will be modified to include the certificate
Execution
- Enforce the execution of signed scripts.
Set-ExecutionPolicy AllSigned
- You can run your signed scripts. If the script is modified, you will need to sign your script again.
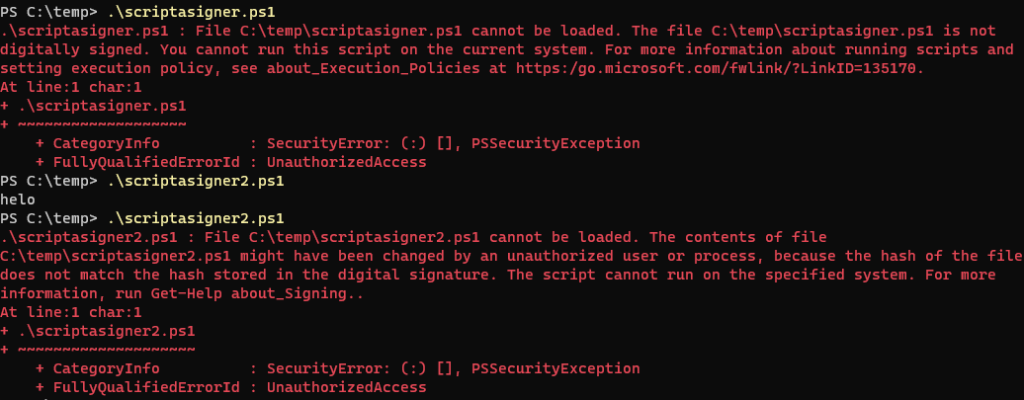
Execution on Another computer
Certificate export
#C'est la même variable que pour la création du certificat en debut d'article
$NomSujet = "ScriptPowerShell"
$PathCertToUse = "Cert:\LocalMachine\My\" + (Get-ChildItem -Path Cert:\LocalMachine\My -CodeSigningCert | Where{ $_.Subject -eq "CN=$NomSujet" }).Thumbprint
PS C:\temp> Export-Certificate -Cert $PathCertToUse -Type CERT -FilePath C:\Temp\ScriptPowerShell.cer
Manually import the certificate
#Importer le certificat pour la machine
Import-Certificate -CertStoreLocation Cert:\LocalMachine\My\ -FilePath "C:\temp\ScriptPowerShell.cer"
# Importer le certificat dans "Autorités de certification racine de confiance"
Import-Certificate -CertStoreLocation Cert:\LocalMachine\Root\ -FilePath "C:\temp\ScriptPowerShell.cer"
# Importer le certificat dans "Éditeurs approuvés"
Import-Certificate -CertStoreLocation Cert:\LocalMachine\TrustedPublisher\ -FilePath "C:\temp\ScriptPowerShell.cer"
Import By GPO
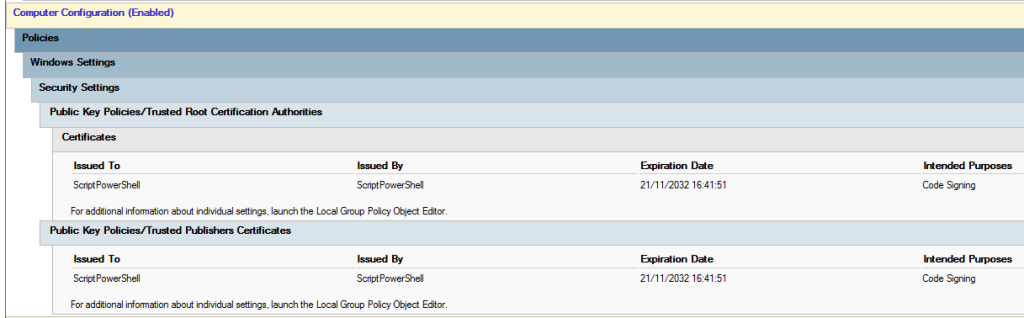
Sign Your PowerShell Scripts with an Internal PKI
Create certificate
On the PKI
- On the PKI, run the following command to create the template (only once).
Add-CATemplate -Name CodeSigning
On Your Computer
- On the computer where the PowerShell will be encrypted, launch an MMC console and open the Certificates module (User).
- Request a certificate.
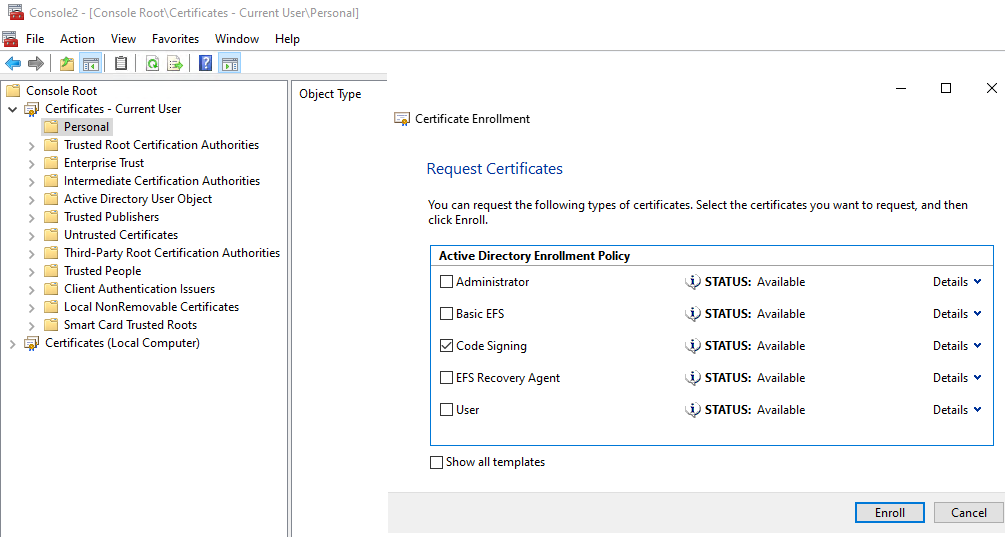
- The certificate is available for 1 year.
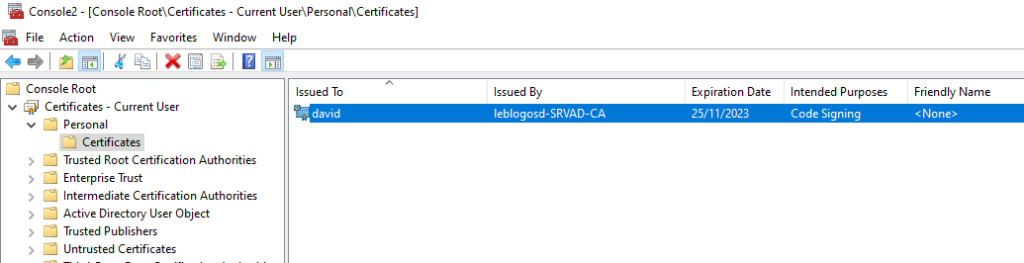
Export the certificate
On the computer where the PowerShell will be encrypted, with the previous MMC console
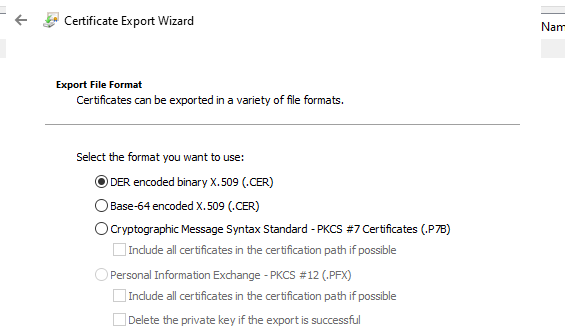
- Select the certificate, then start the export.
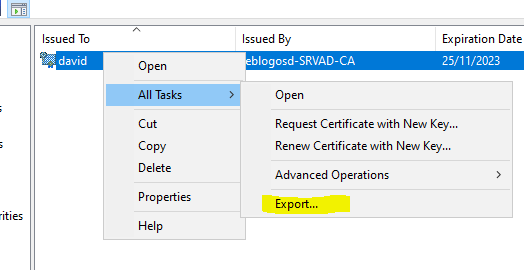
- Select the default options.
Encrypt your PowerShell
On the computer where the PowerShell will be encrypted.
- Enter the commands to encrypt your PowerShell.
$Certificat = Get-ChildItem Cert:\CurrentUser\My\ -CodeSigningCert
$Script = "C:\temp\ScriptAsigner.ps1"
$TimestampServer = "http://timestamp.comodoca.com/authenticode"
Set-AuthenticodeSignature $Script -Certificate $Certificat -TimestampServer $TimestampServer
Execute
- Enforce the execution of signed scripts
Set-ExecutionPolicy AllSigned
- Execution of the script
If you run the script, you will get an error message
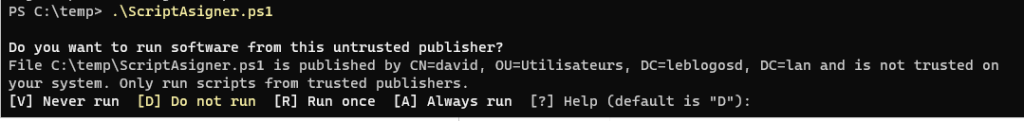
You need to deploy the certificate via GPO to the trusted publishers by GPO
Deployment by GPO
- Create a COMPUTER GPO and deploy the certificate to the “Trusted Publishers”
- Apply the GPO to your computers.
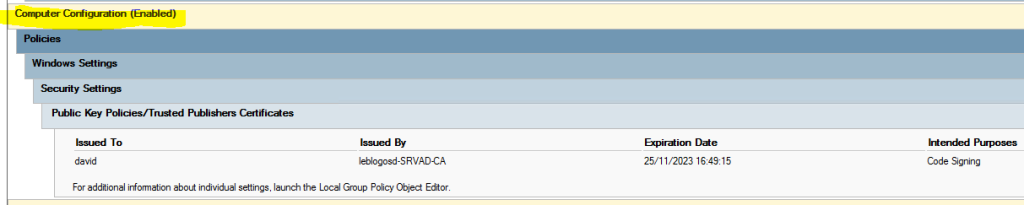
- Launch GPupdate on your computer
Once the GPO is applied, the script executes normally.