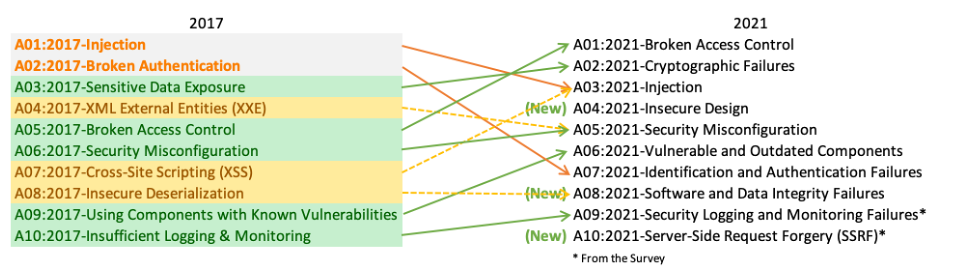
Here’s the OWASP Top 10 list of the most common and critical web application vulnerabilities:
- Broken Access Control: Access restrictions are not properly enforced, allowing unauthorized users to access protected resources.
- Cryptographic Failures: Sensitive data is not adequately protected through encryption or proper key management practices.
- Injection: Malicious data injection, such as SQL injection attacks, allows attackers to execute unintended commands.
- Insecure Design: Security flaws exist due to poor application design, potentially exposing vulnerabilities.
- Security Misconfiguration: Misconfigurations in servers, frameworks, or applications make the site vulnerable to attacks.
- Vulnerable and Outdated Components: Use of outdated or vulnerable libraries and components with known weaknesses.
- Identification and Authentication Failures: Flaws in authentication systems, potentially enabling brute-force attacks.
- Software and Data Integrity Failures: Poor protection against data manipulation, often via insecure third-party dependencies.
- Security Logging and Monitoring Failures: Lack of logging or monitoring, making it difficult to detect attacks in progress.
- Server-Side Request Forgery (SSRF): The application makes unsecured requests to internal resources, potentially exposing sensitive data.
For more details, refer to the official OWASP Top 10 page: OWASP Top 10.

0 Comments