Introduction
Activating BitLocker on a computer is relatively straightforward. The challenge in a corporate setting will be:
- Configuring Active Directory to save the BitLocker keys.
- Activating or configuring the TPM chips.
- Activating BitLocker using a script.
In this post, we will go through the various steps for activating BitLocker on workstations.
Active Directory Configuration
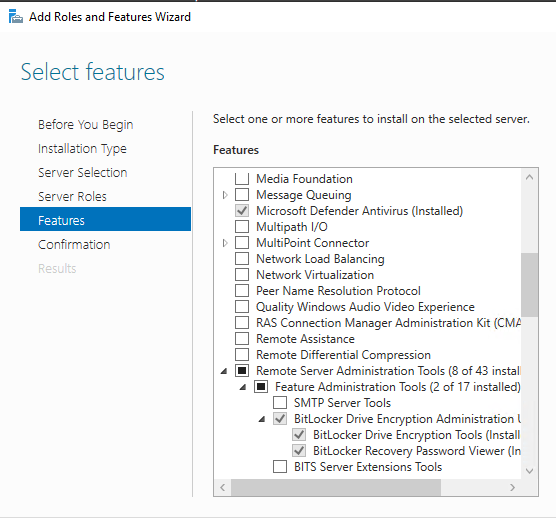
Features Bitlocker install
Installation to be carried out on all workstations managing the BitLocker keys (In addition to the « Users and Computers Active Directory » console).
Powershell
Install-WindowsFeature -Name "RSAT-Feature-Tools-BitLocker","RSAT-Feature-Tools-BitLocker-RemoteAdminTool","RSAT-Feature-Tools-BitLocker-BdeAducExt"
Active Directory Delegation
A delegation is necessary to view the BitLocker keys. We will delegate to a global group in the AD; in our example, it will be « Support Level 2 ».
- Launch the « Active Directory Users and Computers » console.
- Select the « Delegate Control » option.
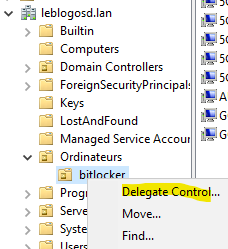
- Sélectionnez le groupe
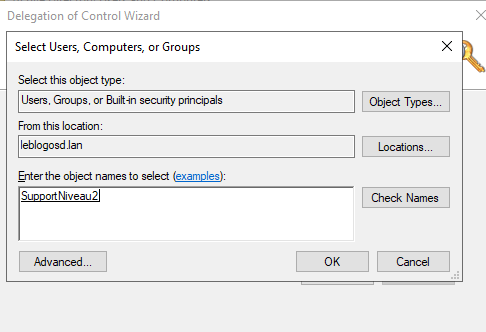
- Select the option to create a custom task.
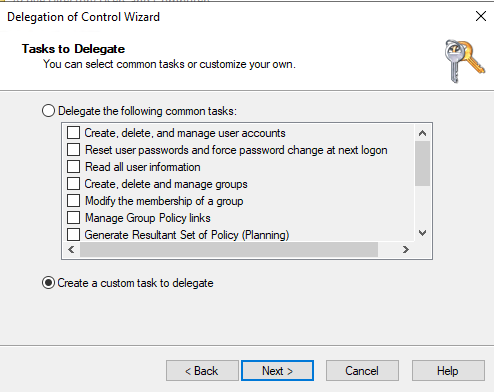
- Select the object named : MSFVE-RECOVERYINFORMATION
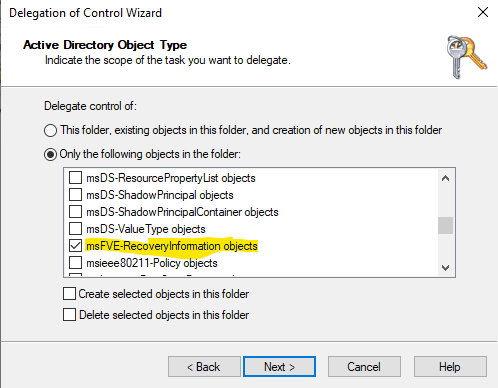
- Select full control.
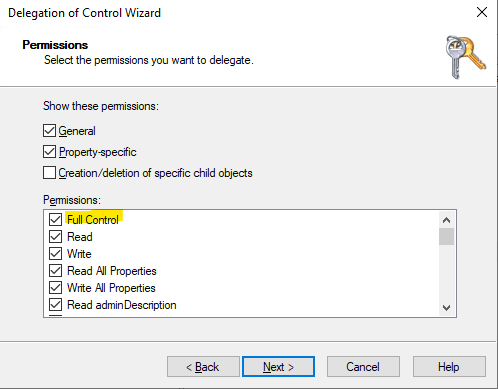
Creation of the GPO to configure BitLocker.
The GPO allows you to specify that the keys should be stored in the AD and the default settings of BitLocker. Creating the GPO will not activate BitLocker on the workstations, so you can set up this GPO at the beginning of your project.
- Create a new GPO with Group Policy Management (gpmc.msc) and link it to an OU where your computers are located.
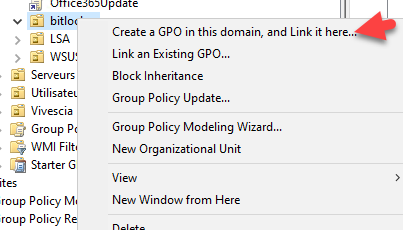
- Indiquez un nom
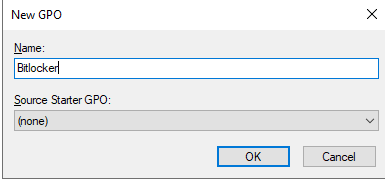
- “Computer Configuration” \ « Administrative Templates » \ « Windows Components » \ “Bitlocker Drive Encryption”
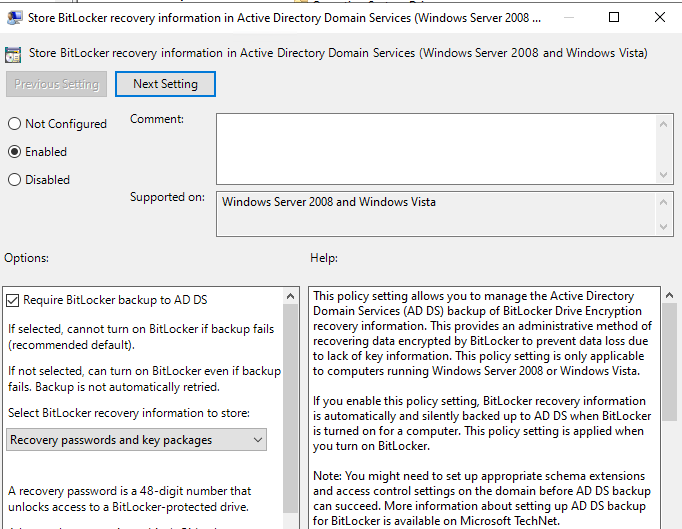
- Store Bitlocker recovery information in Active Directory Domain Services
- Enable
- Store Bitlocker recovery information in Active Directory Domain Services
- “Computer Configuration” \ « Administrative Templates » \ « Windows Components » \ “Bitlocker Drive Encryption”
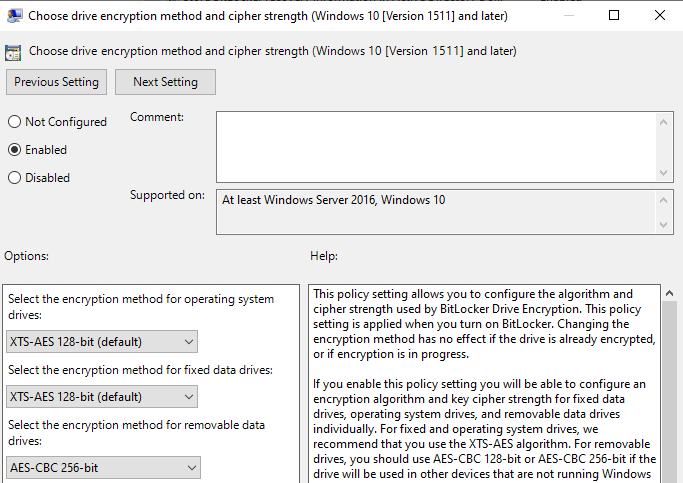
- Choose drive encryption mothod and cipher strength
- Enable => Configurer la méthode de cryptage
- Choose drive encryption mothod and cipher strength
- “Computer Configuration” \ « Administrative Templates » \ « Windows Components » \ “Bitlocker Drive Encryption” \ “Operating System Drives”
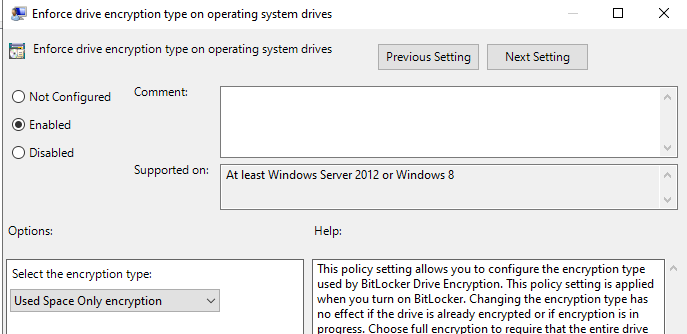
- Enforce drive encryption type on operating system drivers
- Enable => Use Space only encryption
- Enforce drive encryption type on operating system drivers
- “Computer Configuration” \ « Administrative Templates » \ « Windows Components » \ “Bitlocker Drive Encryption” \ “Operating System Drives”
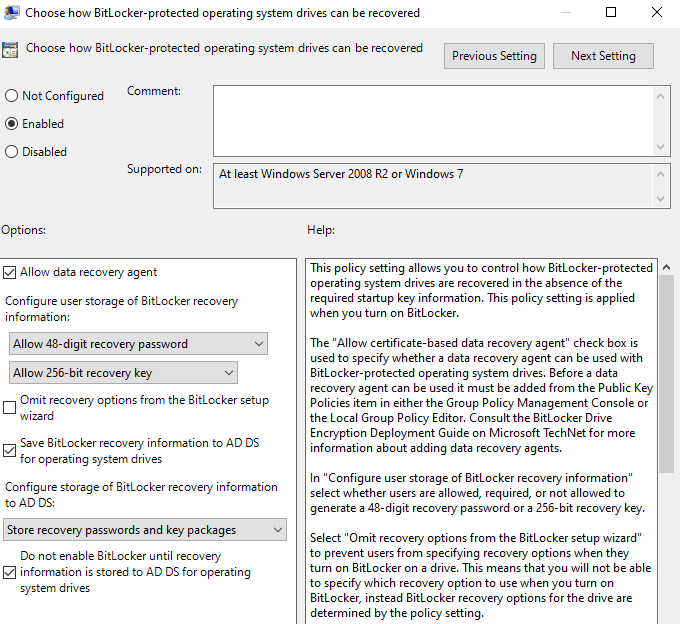
- Choose how Bitlocker-protected operating system drives can be recovered
- Enable
- Save Bitlocker recovery information to AD DS for operating system drives
- Store recovery passwords and key packages
- Enable
- Choose how Bitlocker-protected operating system drives can be recovered
Computer Configuration
Requirements
Management of TPM chips.
In most cases, TPM chips are already activated on computers, especially with TPM 2.0 chips.
- Activating the TPM chips is a prerequisite for enabling BitLocker.
- Activation of TPM chips : Activation des Puces TPM
UEFI Computer
It is recommended that the computer be in UEFI mode. This has become mandatory since Windows 11, but care must be taken with older Windows 10 machines.
Here is a script to detect UEFI mode.
BitLocker Activation
Manually
From the file explorer, you can enable or disable BitLocker.
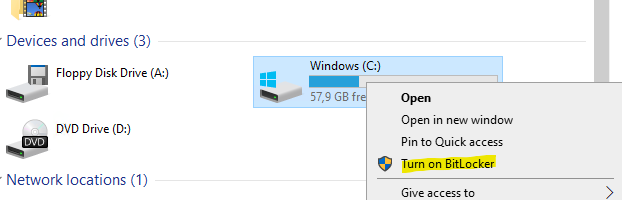
By script
Warning: If the computer has a pending reboot, it’s better to wait before activating BitLocker. The BitLocker Suspend mode can be poorly managed in some cases.
Here is an example of an activation script for BitLocker.
Function Get-PendingReboot {
$isReboot = $False
if (Test-Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\RebootRequired") { $isReboot = $True }
if (Test-Path "HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations") { $isReboot = $True }
if (Test-Path "HKLM:\SOFTWARE\WOW6432Node\LANDesk\managementsuite\WinClient\VulscanReboot") { $isReboot = $True }
if (Test-Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\RebootPending") { $isReboot = $True }
Return $isReboot
}
# ******************** Encrypt Volume ***************************
if (((Get-tpm).TpmReady -eq $True) -and (Get-PendingReboot -eq $false)) {
# ******************* C drive *******************************
# Encrypt volume C
If ($StateC -eq "FullyDecrypted") {
Write-host "Enable Bitlocker on C Drive"
add-bitlockerKeyProtector -mountPoint "C:" -TpmProtector
Enable-BitLocker -mountPoint "C:" -EncryptionMethod XtsAes128 -RecoveryPasswordProtector -SkipHardwareTest -ErrorAction SilentlyContinue
}
}
The complete script for activating BitLocker is available. : Repository/Bitlocker/ScriptActivation
If BitLocker is already activated
If BitLocker was activated before the implementation of the GPO, you can force the key registration in PowerShell.
$BLV = Get-BitLockerVolume -MountPoint "C:"
Backup-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId
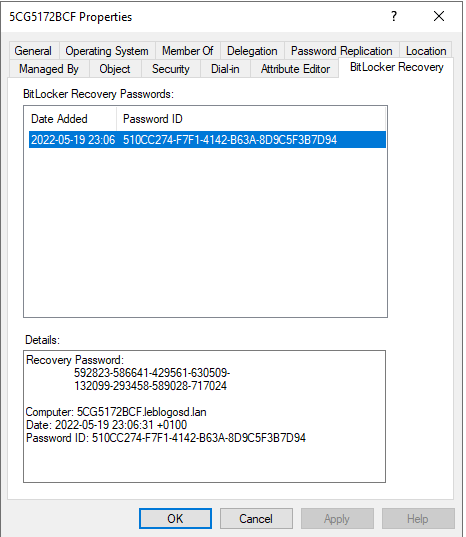
Retrieval of the BitLocker key.
From the « Active Directory Users and Computers » console, the BitLocker key will be available.
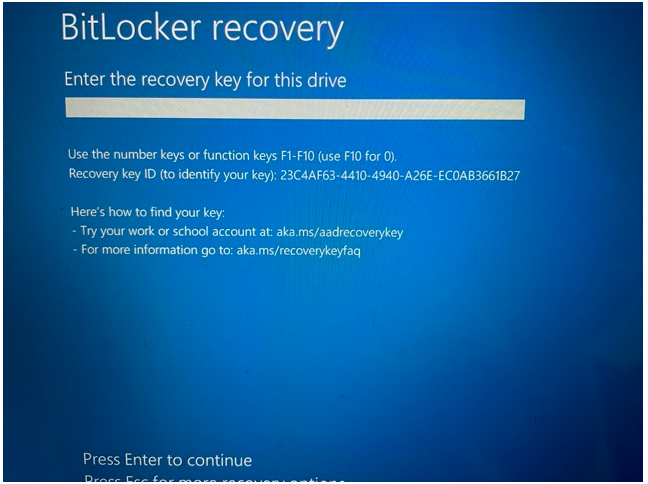
If a problem occurs on the computer, it will ask for the decryption key.

0 commentaire