Introduction
This guide shows how to generate SSH keys with PuTTYgen, connect to a TanOS appliance over SSH with PuTTY (tanadmin / tancopy / recovery), and transfer files with WinSCP using key-based authentication. All screenshots are kept below.
PuTTY
Install PuTTY & PuTTYgen
- Download: https://www.putty.org
- Install both PuTTY and PuTTYgen on your admin workstation.
Generate SSH keys with PuTTYgen
- Launch PuTTYgen (PuTTY Key Generator).
- Recommended: select Ed25519. If legacy compatibility is required, choose RSA 4096.
- Click Generate and move your mouse to create randomness.
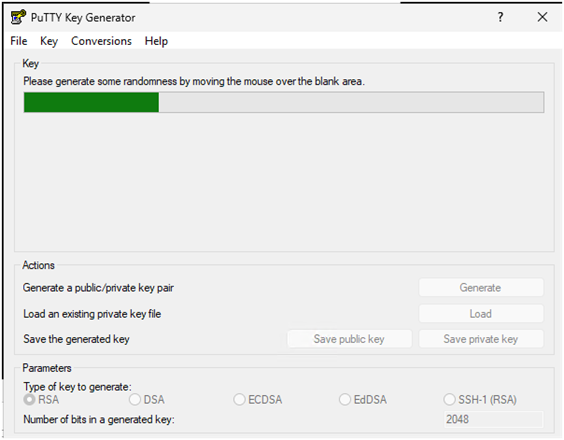
Create multiple keys (recommended)
- One key for tanadmin
- One key for tancopy
- Optionally, one key for recovery (user created later in TanOS)
Save private key & copy public key
- Click Save private key → store securely (set a passphrase if possible).
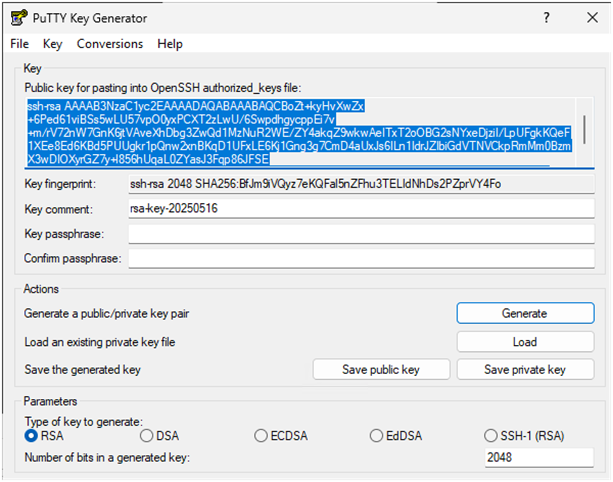
- Copy the public key from the top box (you’ll paste it in the TanOS user’s SSH key settings).
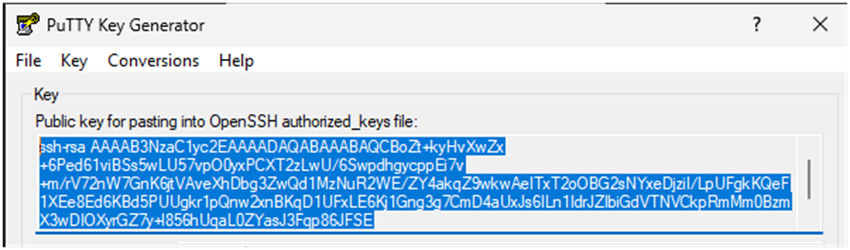
Tip: Use Pageant (PuTTY authentication agent) to cache your key and avoid repeated passphrase prompts.
Connect to TanOS with PuTTY (SSH)
Connection
- Open PuTTY.
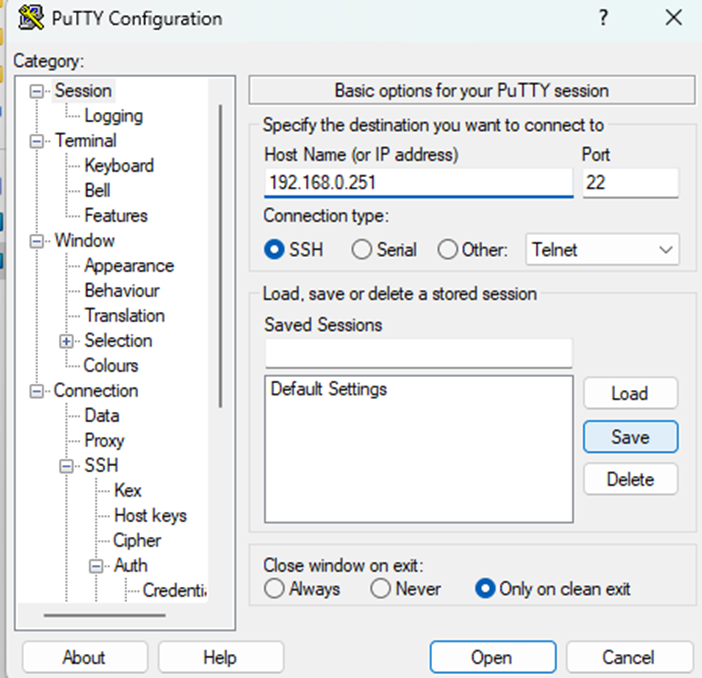
- Session (left): enter the TanOS Host Name (IP or FQDN).
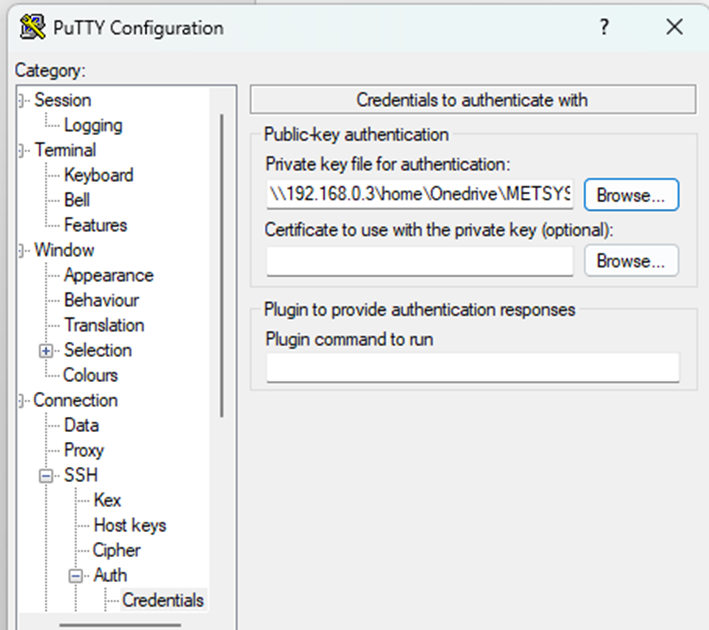
- Go to Connection > SSH > Auth → set Private key file for authentication to your
.ppk.
Save a session profile
- Back to Session → name it (e.g., Tanium-Server1) → Save.
Connect
- Click Open to start SSH.
- At first connection, verify and accept the server’s host key fingerprint.
- When prompted, enter the username tied to the key (tanadmin, tancopy, or recovery).
- No password is required if the key matches.
Transfer files with WinSCP (SFTP)
Session
- Launch WinSCP.
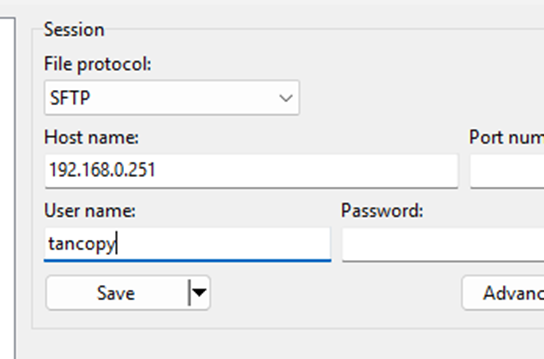
- File protocol: SFTP.
- Host name: TanOS IP or FQDN.
- Username: tancopy.
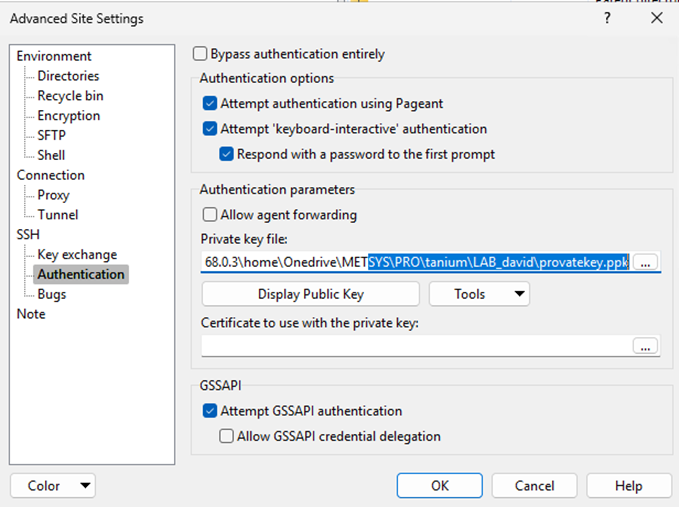
Use the private key
- Click Advanced… → SSH > Authentication → Private key file → browse to your
.ppkfor tancopy. - OK to return to the main screen.
Save and connect
- Click Save (e.g., name it Tanium tancopy). If your key has a passphrase, you’ll be prompted at login (or use Pageant to cache it).
- Double-click the saved session or click Login to connect via key-based authentication.
Security tips: Prefer Ed25519 keys; use strong passphrases; keep private keys off shared drives; and consider disabling password authentication on the appliance once key-based access is confirmed.