History of a website with Wayback Machine
Select a date from the calendar to see the website as it appeared on that day.
Get resources used on a website with BuiltWith
Generate a report and list the technologies, frameworks, scripts, and other resources used by the site.
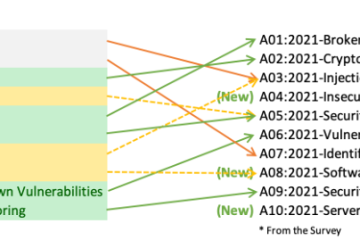
Top 10 Web Security Vulnerabilities
OWASP Top 10 list of the most common and critical web application vulnerabilities
Resource : LOLBAS and GTFOBins
Discover the LOLBAS and GTFOBins projects, tools that penetration testers use to exploit native binaries for privilege escalation, command execution, and data exfiltration.
Pentesting – WordPress – Wpscan
Create a free account on WPScan to run security scans on WordPress sites. Learn to install Kali Linux and perform tests using WPScan with API tokens.
RSS security alert
Securely track security alerts and RSS feeds with FreshRSS on Docker for Synology. Learn to set up a CNAME, configure a reverse proxy, and stay updated on cybersecurity news.
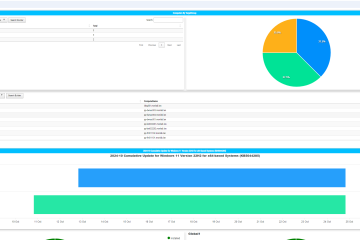
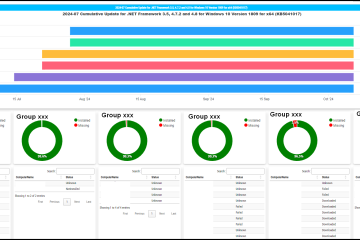
Creating a WSUS Dashboard
Create a detailed WSUS HTML dashboard with PowerShell, including configuration, task scheduling, and IIS virtual directory setup.
Automating WSUS with Powershell
Learn how to automate WSUS patch assignment to different target groups using PowerShell scripts and scheduled tasks.
Complete Guide: How to Install and Automate WSUS
A detailed guide to installing and automating WSUS (Windows Server Update Services) for Windows, covering setup, patch deployment automation, and monitoring via dashboards. Perfect for streamlining patch management.
Install Pfsense
This guide provides detailed steps for downloading, installing, and configuring pfSense on a virtual machine. It includes setting up two network cards—one for internet access and the other for a local network—and initial configurations like disabling DHCP and setting the DNS.
Install Oracle Linux
A step-by-step guide to downloading and setting up Oracle Linux 9.4.0 in a virtual machine, including configuring settings such as RAM, network, and disabling secure boot. Ideal for users looking to create a virtual environment for testing and development.
Install Parrot OS
Step-by-step guide on how to download and install Parrot Security OS on Hyper-V. Includes detailed instructions for setting up a new virtual machine, configuring network settings, selecting installation options, and completing the installation process to have Parrot OS ready for use.
Install Kali Linux
This tutorial guides you through setting up Kali Linux on a Hyper-V virtual machine. Step-by-step instructions and images help ensure a smooth installation, from selecting the installer to configuring the GRUB loader, making it ideal for users setting up a secure testing environment.
How to Retrieve Your KMS Host
This blog post guides IT administrators on how to retrieve and verify the Key Management Service (KMS) host name using PowerShell. It covers how to perform a ping test and check port connectivity to ensure the KMS host is properly communicating within the network.
Display Top Error Computers With powershell
Learn how to use a PowerShell script to display computers with the highest error history from WSUS. This guide provides step-by-step instructions and the full script for generating and analyzing error logs.
Debugging: Generate a Windows Update Log
Learn how to generate and merge Windows Update log files using PowerShell. This guide provides step-by-step instructions to create a detailed log file for troubleshooting Windows Update issues.
Uninstalling Windows Updates (PowerShell)
This article provides a script that searches and uninstalls Windows Update packages based on a given KB number
Command-Line Exclusions in Windows Defender
command-line instructions to add specific exclusions to Windows Defender.
Automated WSUS Cleanup
Learn how to efficiently cleanup your WSUS server using a Powershell script. Automate WSUS maintenance tasks, ensuring optimal performance and freeing up server resources.
Verifying TLS 1.3 Implementation on Client Machines
TLS 1.3, Client Verification, Web Browser, Windows Commands, Cipher Suites, Windows 11, Security, TLS_AES, TLS Cipher Suites
How to Connect to its Integrated Database (BDD) with Powershell
Discover how to connect to the integrated database (BDD) of WSUS using specific server paths. The article provides detailed instructions, including the necessary Powershell script.
Incorrect client Version Displayed in WSUS
In WSUS, there may be instances where the incorrect client version is displayed. This article clarifies the version shown.
Windows update avec PSWindowsupdate
Explore the process of managing Windows updates using the PSWindowsUpdate PowerShell module. The article provides detailed instructions on installing the module, both manually and using standard methods, and offers insights into its utilization for checking update settings, installing patches, and viewing update history.
TPM Chip Activation Across Platforms
A comprehensive guide on how to activate TPM (Trusted Platform Module) chips across various platforms including Dell, HP, Hyper-V, and VMWare Workstation. The article provides detailed PowerShell scripts, methods, and insights for enabling TPM security in different environments.
Move the Integrated WSUS Database
Explore two efficient methods to move the integrated WSUS database: using SSMS and sqlcmd. The article provides step-by-step instructions, including stopping services, detaching and attaching the database, and ensuring proper permissions. It also offers links to essential tools for the process.
Install WSUS Server
Dive into a detailed guide on setting up and configuring Windows Server Update Services (WSUS). Learn about automated patch approvals based on groups, and ensure your enterprise systems stay updated and secure.
Implementing BitLocker in a Corporate Environment
A comprehensive guide on deploying BitLocker in a business setting, covering Active Directory configuration, TPM chip management, and automated BitLocker activation using scripts.
Manage LAPS Configuration Using MSI
To set up LAPS on a domain controller, start by installing it with management tools and extend the AD schema using PowerShell commands. Set up a central store for ADMX files and create a GPO to manage local admin passwords. Give appropriate permissions for reading and resetting passwords in AD, and install LAPS on client computers using a GPO for automatic password backup in AD.