Patch Deployment Ring
Example of a ring-based patch deployment strategy using the software

Example of a ring-based patch deployment strategy using the software
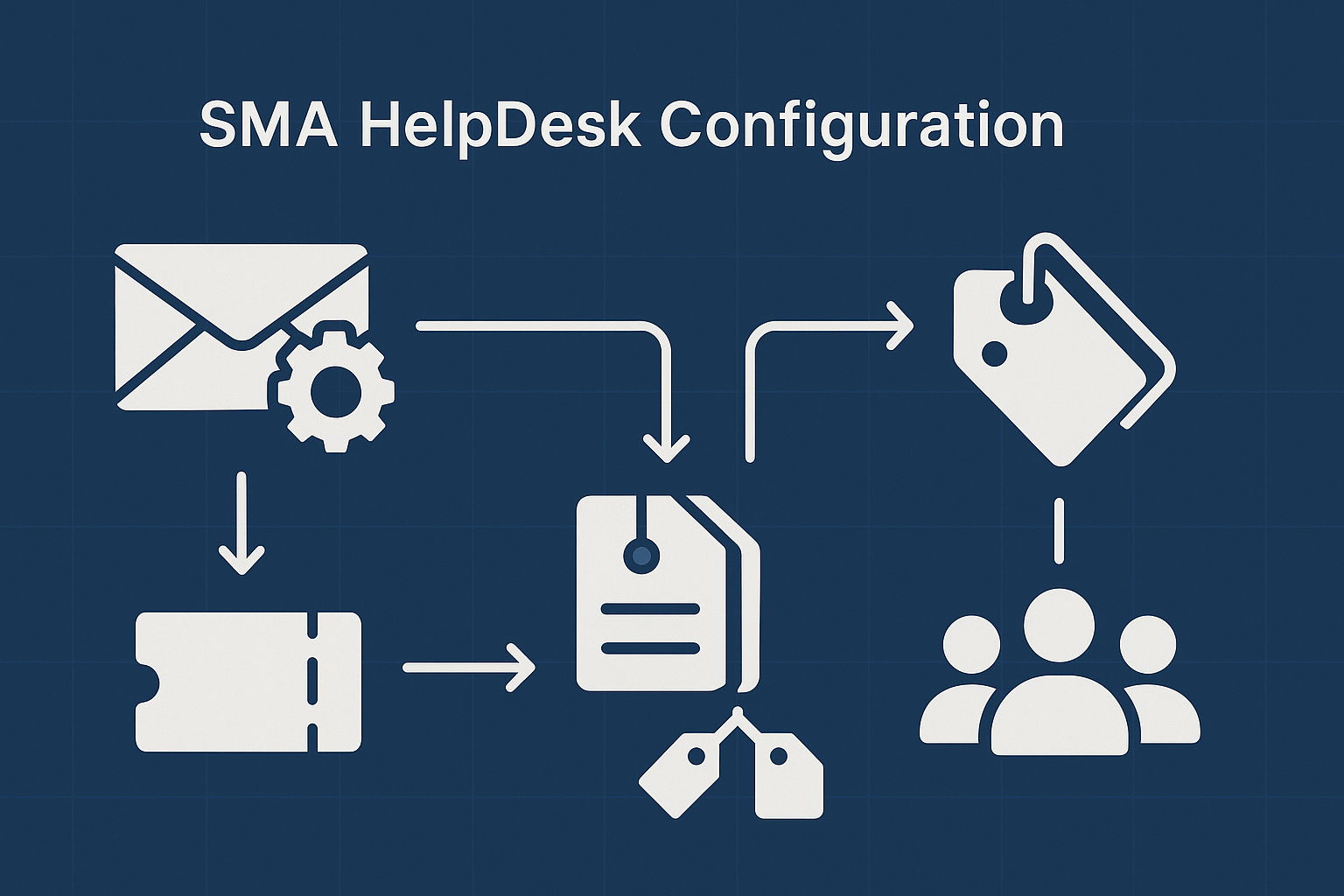
Configuring the KACE SMA HelpDesk module.

Explores three methods to utilize scripts in SMA,

Setting up remote access via UltraVNC and Windows Remote Assistance.
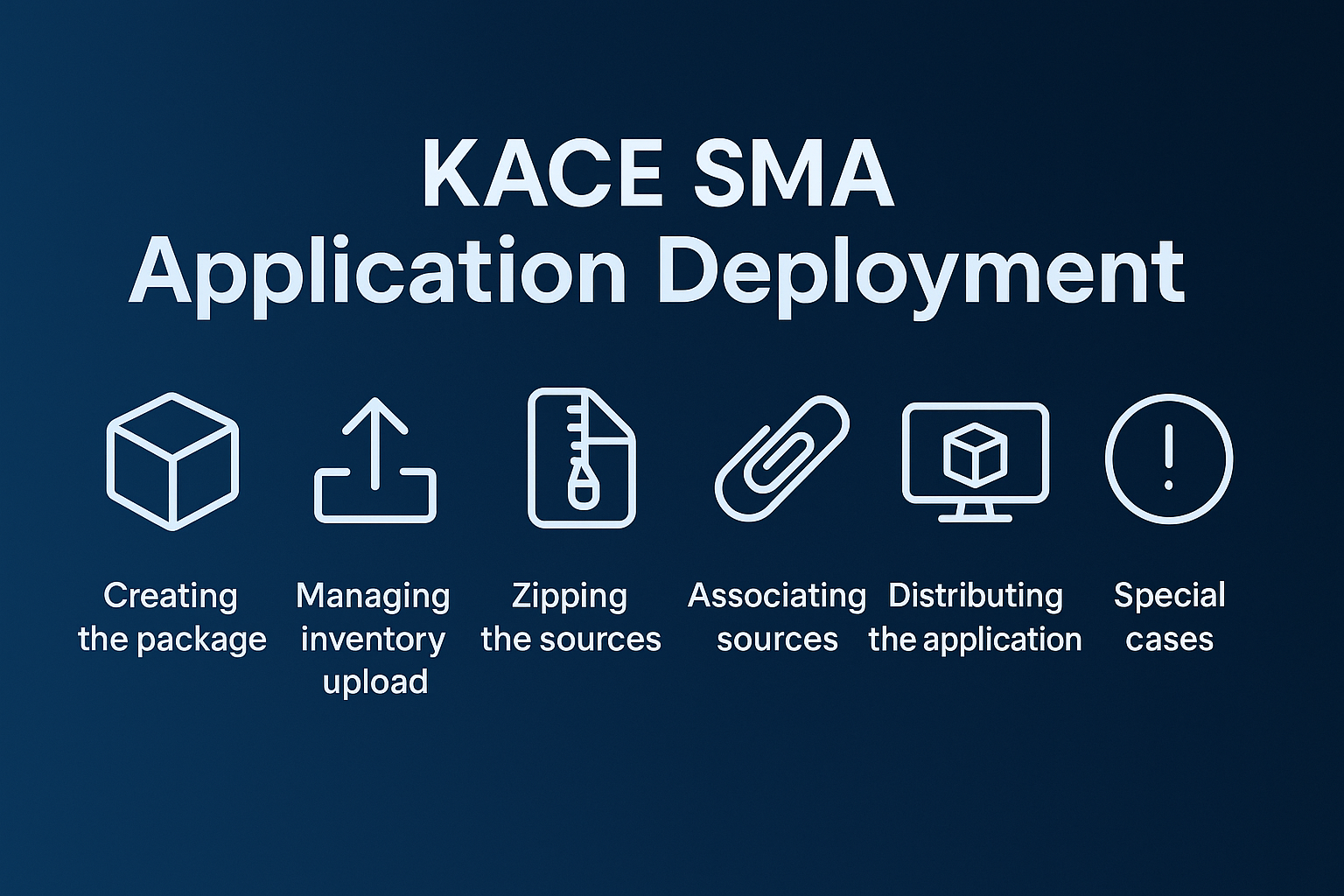
Managing application deployments with KACE SMA
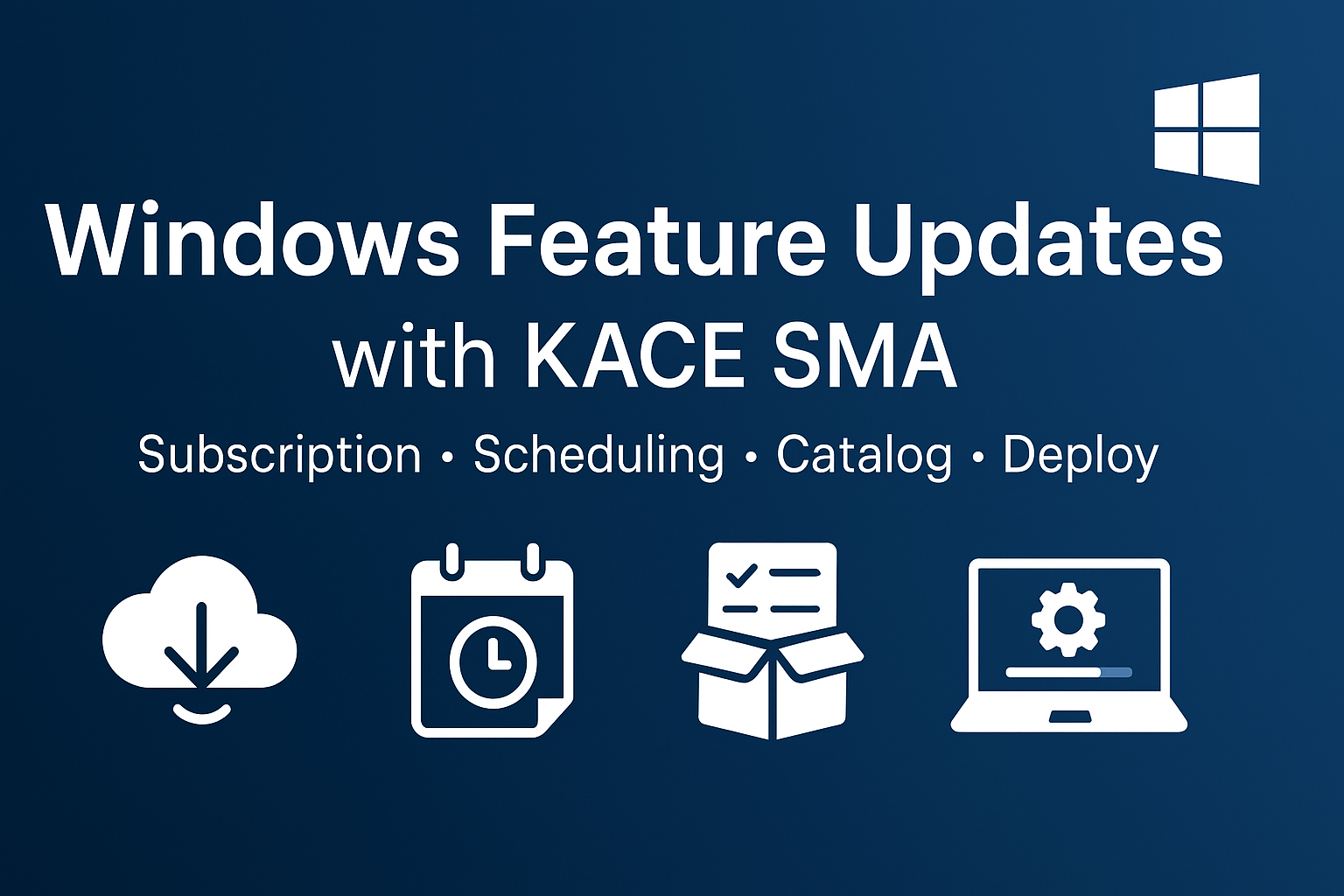
Managing Windows release changes using the KACE Systems Management Appliance (SMA).
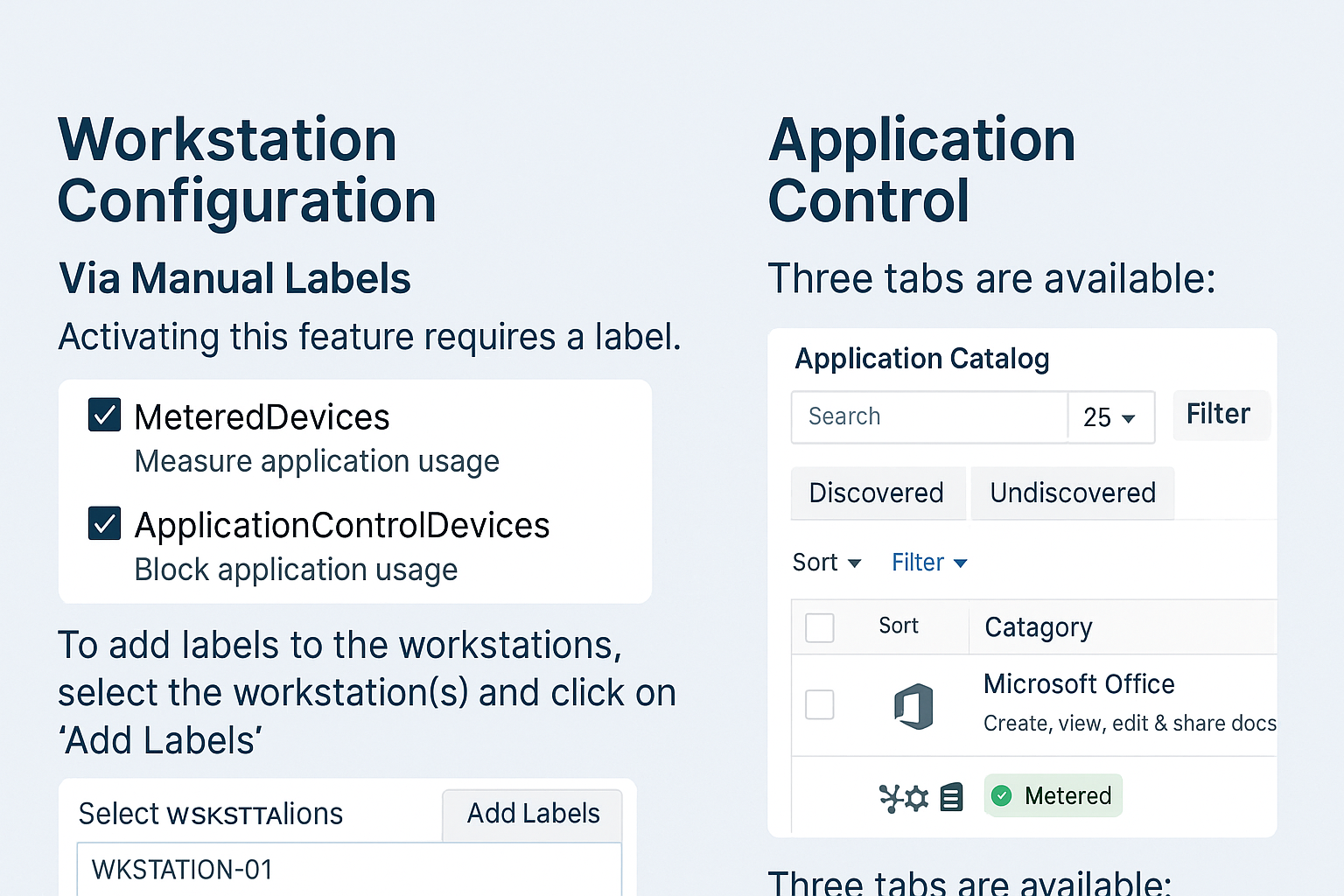
Managing and controlling licenses with KACE Systems Management Appliance (SMA).

Managing and monitoring the TPM chip and BitLocker encryption status using Systems Management Appliance (SMA).
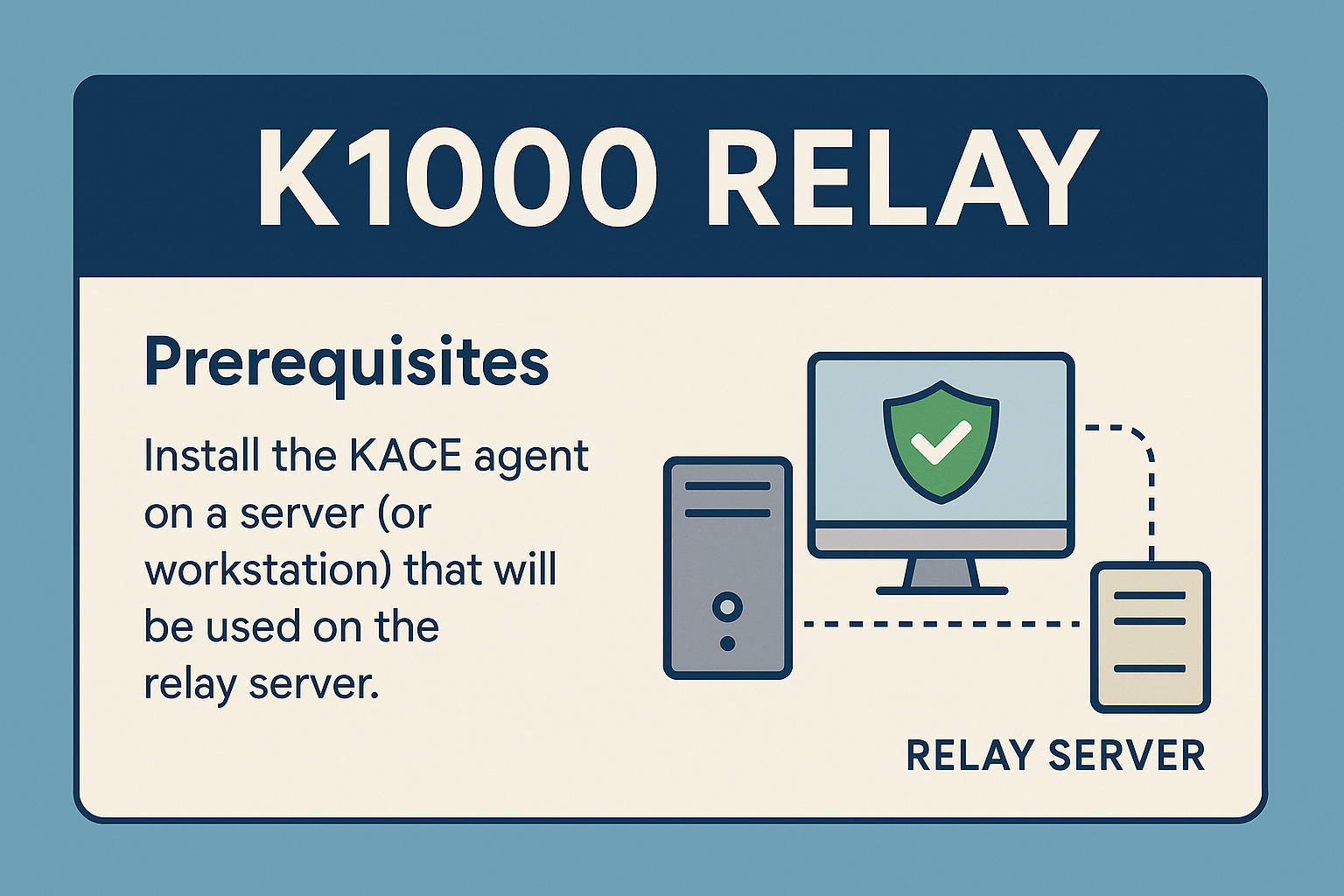
Configuring and installing a remote relay with KACE SMA.

Enabling and configuring server monitoring in Quest SMA.
Installing and configuring Quest SMA appliances, including network setup, agent deployment, backup.
Available at Google Play and the App Store, the free KACE Go Mobile App